GPU Password Cracking – Bruteforceing a Windows Password Using a Graphic Card
GPGPU computing is getting lots of attention these days. GPGPU computing simply means doing general calculations on graphic cards (GPUs) rather than CPUs. Traditionally, GPUs were used only for getting graphical output, rendering frames in games and other purposes related to graphics. Lately, people started realizing that GPUs are far more efficient at handling highly parallel tasks and that there should be a way to code for graphic cards. Though GPGPU computing is still at its infancy, a lot of progress has been made toward this direction. For example GPUs are used to speed up video conversion, video processing, doing scientific calculations, folding and password hash cracking.
The last one – password cracking looks very interesting and we are going to discuss about just that. Recently I came across a free password hash cracker called ighashgpu. This tool is developed by a guy called Ivan Golubev. It’s a command-line utility meaning, there is no GUI. Though allergic to command-line utilities, curiosity made me to meddle with the tool to see how fast my Radeon 5770 would crack passwords and the results are simply amazing.
The tool supports these hashes;
- Plain MD4, MD5, SHA1.
- NTLM
- Domain Cached Credentials
- Oracle 11g
- MySQL5
- MSSQL
- vBulletin
- Invision Power Board
- and more …
Cracking an NTLM Password Hash with a GPU
I’m going to use the NTLM hash here. If you are wondering what NTLM is, your Windows (NT and above) logon passwords are not stored as plain text but encrypted as LM and NTLM hashes. They are not reversible and hence supposed to be secure. LM hashes can easily be broken using Rainbow Tables but NTLM hashes are relatively stronger. But that’s not stopping us from cracking them.
For comparison, I’m going to use another popular and free security tool – Cain & Abel. This is an excellent tool for breaking different passwords, using the CPU.
To crack a password, you need to have the NTLM hash of that password. Fortunately, Cain & Abel has a hash calculator. So let’s do some password cracking.
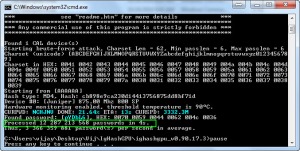
A password with 5 characters
Using Cain, I generate a random password “fjR8n” whose NTLM hash is “AA8251D1BB587ABFAE6403194216041F” without quotes of course.
Now that the password has upper, lower case letters and a number. So the character set should be like this in Cain to crack the password.
As you see, Cain has taken about 24 seconds to crack the password at the rate of 9.8 million passwords/sec.
Let’s see what ighashgpu has to offer.
The password is found in less than one second. Secondly look at how many passwords the GPU has churned out per second. Dude, it’s 3.334 billion passwords.
A password with 6 characters
Let’s now take “pYDbL6” as the 6 character password. The NTLM hash for that password is CB898E9CA230D14413756875DD8BF71D.
Now that Cain reports it would take approximately 1 hour and 30 minutes to crack our password. Note that this is the maximum time Cain would take to crack the password. It could even be less than that, depending on the password.
What about ighashgpu?
Ighashgpu finds the password in staggering 4 seconds. Also note that the maximum time it would take to crack a 6 character alphanumeric password is about 17 seconds. See the difference between GPU and CPU computing?
A 7 character password
Let’s take “fh0GH5h” as the 7 character password whose NTLM hash is 29152D8B2EB5806302EB5829635309E6.
Cain would take about 4 days to crack the 7 character alphanumeric password.
But ighashgpu would take about just 17 minutes and 30 seconds maximum to crack the password hash. Also note that the password is already found in 2 minutes and 15 seconds. This means, my GPU would only take 17 minutes and 30 seconds max to crack ANY 7 character alphanumeric password.
An 8 character password
Let’s make things more interesting now. I take “t6Hnf9fL” as the 8 character alphanumeric password whose NT hash is 7B0E126699A3EE5F0108D07926448E47
Aargh, Cain would take almost one year to crack that password.
What about ighashgpu?
Isn’t it astonishing? Ighashgpu can crack this hash in 18 hours and 30 minutes.
Okay, let’s give some challenge to my GPU.
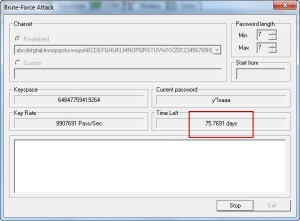
A 9 character password
Our candidate here is “kfU64FdB8” – 75A7AF26871E71BCF853509C47DB3475
Err, you have to wait for more than 43 years before you find the password if you use Cain.
Let’s move on to ighashgpu.
Isn’t 48 days better than 43 years?
Okay guys, we just saw that a Radeon 5770 GPU would take 48 days to break a 9 character password. My tests also revealed that a 5770 would take 8 years and 70 days to break a 10 character alphanumeric password. Now it’s time to add special characters to the mix.
First thing first. Our 7 character mixed symbols password and it’s hash “F6&B ls” (note the space) – B438599AC14AB16E2F889A4471F7C76F
Cain will take 75 days.
Ighashgpu wouldn’t even take 7 hours to finish the job.
What about an 8 character password?
While Cain would take more than 19 years, ighashgpu can crack the password within 26 days. Far better.
Okay guys, we have just seen what ighashgpu can do for us. It’s fast, really fast indeed for password cracking, since it uses GPU. It can crack any simple and short password and even a simple 10 character password within acceptable time limits. With GPUs becoming more and more powerful, things are only going to get worse. So what length is safe? Can we say a 12 character password is safer? Maybe, but chances are there that we may choose mixture of common words (like names and numbers) as long passwords which may be easily broken with a simple dictionary attack.
If your password contains just numbers, even if it’s 10 characters in length, it can easily be broken with ighashgpu. Let’s take a random 10 character numeric password – “8457317452” whose NT hash is 1089F7DE94ABEE2F38BFBA428C782905.
Look at the image. It’s horrible to know that this password is broken in less than two seconds!
Now I’m running out of patience to know how long my GPU would take to crack mixed (all symbols found on an US English keyboard) 8 character password.
Password: g&4K 3gI
Hash: 02944DC7857DFDDDE7DE6FDF38E9CC95
Just a little more than 25 days.
What about a 9 char password?
Password: H<k7$6fVJ
Hash: 4F5BBAB78A3551E369E205A3022920E9
Now it’s almost 7 years.
Got the drift? The more complex the password is, the longer the GPU will take to crack the password. So when you choose a password, make sure you don’t choose common words and names and always mix your password with letters, numbers and symbols.
We have just witnessed the power of a GPU against a CPU. GPUs are really fast and highly parallel. My Radeon 5770 is not the fastest card around but packs way more punch than a traditional CPU. It also looks like Radeon cards are faster than their Nvidia counterparts especially when it comes to password brute forcing and the latest Radeon 6990 graphic card should be several times faster than my Radeon 5770 and should make ANY 8 character password obsolete.
Have a look at my GPU in action.
Disclaimer:
As interesting as it may seem, password brute forcing can also be used for illegal purposes. I request you not to use the steps provided here for cracking others’ passwords and I take no responsibility for that.















While I agree that GPGPUs are ideally suited for this type of thing, I think a lot of the difference you’re seeing comes down to the amount of skill and effort put into the NTLM cracking functionality by the authors for their respective products.
ighashgpu is a single-purpose tool, whereas C&A does many things. My impression is that C&A is mostly used with rainbow tables (supplied elsewhere), whereas the author of the GPU tool is set on being the best.
Last time I looked into it, my impression was that a modern CPU could probably be made to run *no slower than* 5-10x that of a modern GPU at this type of task. Faint praise, I know 🙂
As OpenCL matures, I suspect we’ll see code written which can be benchmarked on both. Exciting times!
Well, I haven’t compared Cain vs ighashgpu. It’s between CPU and GPU and Cain happened to be the tool to compare the CPU power to GPU. While Cain is an excellent security tool, I wish the makers of it even support GPUs for password cracking.
You can cut the processing time down by optimizing the password generation. You can identify the common password patterns and then generate passwords following these patterns. I give an introduction for these techniques with John The Ripper on my blog here: http://codebazaar.blogspot.com/2011/05/why-we-need-strong-p4ssw0rds.html
Reminds me of dictionary attack.
The dictionary attack is probably the first thing to try. But companies are enforcing password rules such as: you must have at least a lowercase, uppercase and special character. What’s going to happen? A bunch of users will choose a dictionary word, the first character will be uppercase and there will be an exclamation mark at the end 😀
You forgot to mention that salting passwords makes all of this irrelevant.
Yes salting makes bruteforcing harder but it’s still possible. The reason I have used NTLM here is it’s relevant to most of us because 95% of us are using Windows.
Awesome read. Check out the nvidia tesla M series cards (2050/2070)
I think Radeons are faster than Teslas for password cracking and far cheaper too.
Could ighashgpu take advantage of bridged Gpu’s via SLi or CrossFire?
I’m just wondering if you could double or triple the speed via bridging.
Yes it can.
Illuminating stats. NTLM hashes from a compromised machine ought to be simpler to crack using GPUs. But I don’t think it’ll be trivial to obtain NTLM hashes in an enterprise setting that easily. Do you?
I hope Microsoft checks out your findings as a way to improve their product.
Cheers,
@gsvolt
It may not be that easy to obtain NTLM hashes in an enterprise setting but it’s still possible. If there is a working DVD drive or a USB port, then the rest is given. Though NTLM hashes from a compromised machine ought to be simpler they in reality are. How many of us are intentionally using a strong 10 character password? As Matthias Buchner said, most of us have the first character uppercase and the last one a symbol, especially !@#.
Maybe websites/applications can start telling you how long it would take to crack your password. That may make people try a little harder:
Password: Chrysler!
*I would take 2 seconds to crack your password. Are you sure?
Password: #S#%f%)!2
*I would take 7 years to crack your password. Good job!
Nice work! Have you run any tests on other hashing algorithms? I would be very interested to see how ighashgpu (and traditional CPU-based cracking) does on an MD5-hashed password.
ighashgpu does well on MD5 hashes too. Not as fast as on an NTLM but about 1.9 billion passwords per second.
Even 7 characters are not safe OMG. I have to improve my brain to remember bigger passwords. Thanks for heads-up.
The University of Georgia was experimenting with this last year. http://www.gtri.gatech.edu/casestudy/Teraflop-Troubles-Power-Graphics-Processing-Units-GPUs-Password-Security-System
They were able to gang GPU’s to achieve staggering results, even 12 character passwords are crackable in a sort amount of time.
What is “salting passwords”? Thanks.
Basically, it adds a certain phrase to your password, that no one knows.. It makes it extremely difficult to crack a salted password.
It really is frightening how quickly passwords can be cracked. Thanks for sharing this very interesting (and scary) Post.
Hi,
The examples used are “random generated password”. A bruteforce of all possible combinations is the only thing to do.
In the real world, passwords, even complex ones, are NOT random generated. They are created by human person.
For example “F00bar123!!” seems complex regarding to its length and charset. Bruteforce with special chars would take 18.000.000 years with cain and 52.000 years with ighashgpu.
However, we have developed at LEXSI a tools called crackNfast which is a probabilistic oriented rainbow table that can crack this hash in less than 2 minutes. Of course, it took us 3 months to generate the rainbow table (on a 1000$ computer !). But what is 3 months compared to 52.000 years !
Recently, for one intrusion test, we have cracked with our crackNfast rainbow tables the password “RSPassword123$” in 45 seconds (14 chars with mixedalpha+num+specialchar).
Have a look at crackNfast : http://www.lexsi.com/francais/cracknfast (sorry, French version only so far).
Why do I doubt “it took us 3 months to generate the rainbow table (on a 1000$ computer !)”
Really? My two GTX580s ran more than $1k, and I doubt my computer could generate a large rainbow table in 3 months.
If my password is change cycle is shorter in duration than the time required to crack it, I’m not losing much sleep over this. It’s harder to hit a moving target.
In your examples the length of the password and its character set was known. In a real-world case, those would not be known. Wouldn’t that greatly increase the time to crack?
What I have discussed here is, smaller and simple passwords are simply useless against GPU bruteforcing. If a 7 character password can be broken in just a few minutes, I would set the cracking application to search for all possible combinations on keyboard from 1 to 8 characters. If that doesn’t work, I would search all alphanumeric for 9 characters and so on. Though the cracking time depends on the GPU used, future graphic cards can even render 12 character passwords useless.
The IEEE and ACM both have done studies, where they showed the following are ridiculously common:
* Dictionary words, where the letters have been replaced with l33t.
* If you force password rotation, there will be a base password, and then the user will increment some flavor of counter (month, sequential, etc.), and that counter will usually be identifiable.
* The longer the password is, the more likely it is to be written down somewhere in close proximity to the computer
If you want to have even more fun, take a look at peer1’s service offering. You can rent, by the hour, hundreds of thousands of nVidia GPU’s. You can pop four 5770’s in some mainboards, and you can pop four 7700’s for that matter, on the ATI side of the house. Peer1’s facility, though, has 16 per chasis, times some ungodly high number of chasis. Just take a look, that’s all consumer grade equipment.
Just think about it — how many SHA1 sums could you check an hour on the Peer1 GPU cloud?
Could you please give me some examples for ” It also looks like Radeon cards are faster than their Nvidia counterparts ” ?
I am just curious about this and would like to see some numbers, so that the next time I buy my graphic cards, I would know which one to pick.
The context was password cracking. ATI/AMD GPUs are faster than Nvidia cards for password cracking. A Radeon 4770 will be faster than a more powerful Nvidia GTS250. Have a look at here for example http://www.golubev.com/files/ighashgpu/readme.htm. But for gaming, it all depends on the price point.
Mast re Vijay…
Good article to read….
To Peter: Salting a password is when the software which generate the hash of your password also add some additional characters to your password and the hash that password so that no one can really know what the password is ….
my friends, this process is necessary to find a key to the programs offered here Can I? please give me an example of the problem is very important for people to
FFBE00BD3F78F7AE – 65D1C6AD8EBD1A14 = A0A1A2A3A4A5A6A7
which do not belong in the key of the second key switch in the first cw cw that there is a program that finds the public key of a0a1 using them, but very slowly, I would like to offer our help to accelerate this program using
need to find the key
73 18 46 83 25 EC 42 D3 – EF 89 60 D8 A0 0C 43 EF =?
I suspect that things will not change until the People start to question and challenge the status quo.Thanks
Hello,
I am trying to crack my own password which is 10 characters length and i
know the first 6 characters. Why i cannot use the mask xxxxxx???? or a ?xxxxx???? mask?
Thanks!
It is really fast but since i know some of the characters why should i waste time?
If you want to use masks and crack a password with GPU, try Hashcat-gui. It’s similar to ighashgpu but a little faster and more flexible.
Could u plz answer me what i have just asked? Thx
Could any1 pleaz tell me how to recognize whether a hash is md5 or sha1 etc? 😀 Iam new….!
Will it support new Ati Radeon GPU like 6490 or 6770 etc…!?
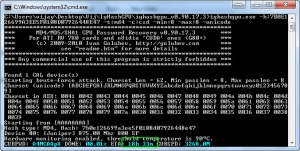
ighashgpu.exe -h:7B0E126699A3EE5F0108D07926448E47 -t:md4 -c:csd -min:8 -max:8 -unicode /cpudontcare
…
Device #0: [GeForce GTX 580] 1880.00 Mhz 512 SP
Device #1: [GeForce GTX 580] 1880.00 Mhz 512 SP
Hardware monitoring enabled, threshold temperature is 90°C.
CURPWD: gYg8AGkp DONE: 00.17% ETA: 7h 32m CURSPD: 8028.3M=4002.0M+4026.3M
🙂
Interesting. You extracted a different password (gYg8AGkp) with the GTX 580’s than Vjay did with the 5770 (A4MCAApX). I assume both are correct, so this is a hash collision, but apparently the combinations were tested in a different order, too.
why is it that when i try to crack some passwards it tells me that no hashes loaded ?
how can i get it for my cain software,?
Hello, can u please recommend me a mobile graphic card for brute force purpose. Which one is better on brute force, ati or nvidia?
And, is there big speed difference between mobile and desktop graphic cards?
Thanks in advance
Hows about 8 last digits of your phone number, followed by your vehicle registration? 15 characters, I’d imagine the pattern has some statistically probable individual characters, but by the large unpredictable… (not my details obviously):-
19435787CD56RTD
With only using alpha-numerics, how much faster is cracking, compared to it being random including all characters/symbols on the keyboard?
Hello, can u please recommend me a mobile graphic card for brute force purpose. Which one is better on brute force, ati or nvidia?
And, is there big speed difference between mobile and desktop graphic cards?
Thanks in advance
a mobile gfx suffers of dust, high temperature, lifetime, if you have the choice always go for a desktop
Can you please let me know how can I hack the website
Don’t you know that it’s illegal?
Hi Vijay
Thanks for your contributions and shared knowledge here!
Being more the business guy than IT, please help me understand the implications better.
What I don’t understand and would like to learn about better without getting a cryptographer:
A. external vs. local
Is hacking a encrypted password on your the local pc harddisk
really respresentative for hacking the same password on
an external webserver with MYSQL MD5 table?
Isn’t there more latency time, other obstacles online than locally at home?
B. “only 5 wrong iterations in a row then block account”
There are many forms where one can only put in limited amounts of wrong passwords.
I don’t get why it’s relevant to talk about 9.8Million/sec. when
one has the possibility to restrict access and account even after 5 wrong iterations.
Are there utilities hackers use to circumvent this “only 5 wrong ones”?
Scenario:
An MD5 hashed MYSQL password online on webserver.
Users have to login on a form where if 5 wrong passwords in a row happen account is set on hold and client needs to call in for deblockage.
Questions:
What equipment would someone need on average to break in and
how long would it take in hours estimated?
I would like to hack my own website to get an experience what is needed. Please tell me what the usual break in would need one to do.
Of course I will not use this for any other reasons that self-experimentation on my own website.
have a good day!
matt
Hi, For question A, the answer is a big no. Cracking a hash locally is not the same as doing that online. But why cracking a local hash is important is there are many ways to hack a web server to get access to the password hash table in the database that contains the user name and password hashes of millions of users. If that is accomplished, then a hacker can crack thousands of hashes locally.
Hi Vijay,
A brilliant and a very simple read.
I plan to buy a Lenovo ThinkPad T520 (424049U) having a nvidia quadro nvs 4200m graphics card (1 GB). Could you please comment on its performance for bruteforcing purposes?
Thanks
AMD/ATI cards are simply faster than nvidia cards at this time as far as password bruteforcing is concerned. If you want to get a system for bruteforcing, get a desktop.
Be interested to know how many billions of sha-512 passwords could be checked per second…
nVidia GTX 260 w/ 192 SP peaks at 560M/s MD5 & 175M/s SHA1
AMD (ATI) 7970 peaks at 2730M/s SHA1
Thanks …..
I wrote an article titled “The Brute Force Misconception” earlier this year, and it explains (with some calculations) why brute forcing passwords shouldn’t be given the hype that it gets sometimes. Thanks for not misleading people to think that they can go buy a graphics card and suddenly be able to crack any password they want.
http://security.nathanbowman.us/2012/04/the-brute-force-misconception.html
Hello.
Can you help me?
Can I use broken VGA cards for cracking?
For example: There is a VGA what overclocked and makes errors in the picture/monitor, but works.
Thank you!
You may want to try that. But which one? If it’s a low end card, it’s not worth it as it won’t be fast anyway.
I don’t have like that card. I just thought of this. Because I don’t have money for 4pieces new high end cards. I thought I build a system from broken cards if these are able to crack.
I just need to know one thing.. I need to crack 15-16 digit numeric password but it takes 1 second for my cpu to try 1 password as I need to verify whether the password is right through online storage.Can you just tell me how much time does an GPU takes to do this…
Through online storage? That should be very very slow. If you want to crack something, do it offline.
I know this is about another tool, but Im using Cain to crack my own password in another user of my work pc (which i set 2 hours ago and already forgot)
i know it starts with some letters and then has a 6 digit number (which i DO know)
do you know how i can narrow down the work for Cain and specify that the password starts with letters and ends with those 6 digits?
I have to check. I have used mask attack using some other tool before and I don’t remember which one it is.